Explosion (VIP only)
- Admin
- Apr 1, 2023
- 2 min read
Enumeration
As usual, let's start with nmap
nmap -sV IPReplace IP by the IP of the target machine (Explosion)
Note: The IP of our target machine will change all the time, make sure your replace IP in the command below by the target machine's IP. You can find the target's IP directly from your hack the box account.

We can see port 445 is open, which is associated with SMB. We can find 3 shares but our access is denied for each of them.
Let's look into port 3389. Port 3389 is often used for RDP (Remote Desktop Protocol)
We can use a tool called xfreerdp that will allow us to see the target's screen or display.
Foothold
Let's first use the command:
xfreerdp -h-h for help

Check the line
Usage: xfreerdp [file] [options] [/v:<server>[:port]]
If we ignore [file] and [options] and [port] we end up with the basic command:
xfreerdp /v:10.129.1.13
Press Y and press enter to trust certificate
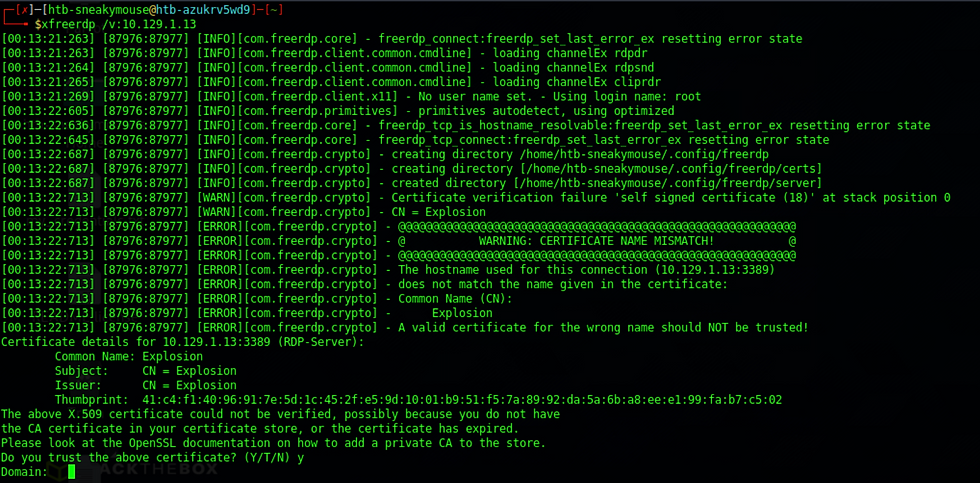
For the Domain let's try the name of the machine which is Explosion
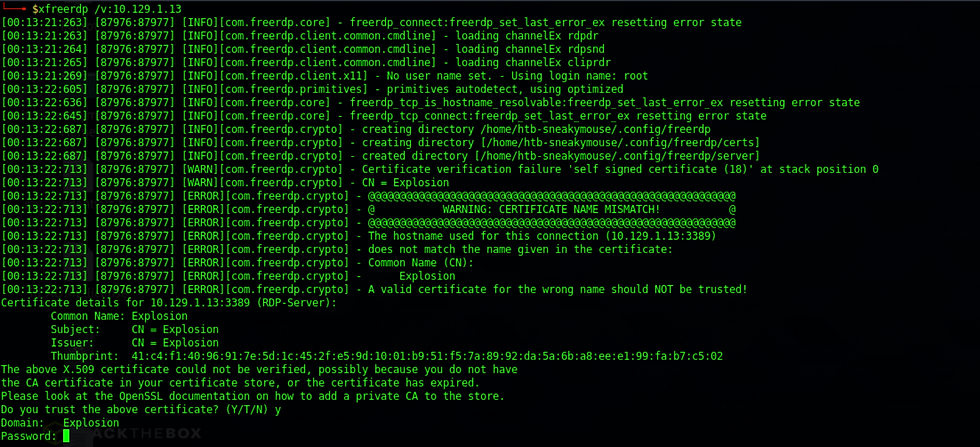
Now we are prompted for the password. If the service has been misconfigured we may be able to login without a password. Let's try our luck and just press enter.

This failed.
With xfreerdp , if we don't provide a specific username, the service will use our VM username as default.
Let's provide a username this time. For instance, admin OR Administrator OR root OR user.
We will use Administrator.
xfreerdp /v:10.129.1.13 /u:Administrator
We do not know the password so let's just press enter
It works! The service was misconfigured and allowed us to get in with no password!

Click on No
Minimize the Server Manager Dashboard and you should now see the Desktop of the target machine:

On the Desktop, there is a file called flag. Let's open it!

You got the flag! Congratulations!


I was stack, didn't know that you had to minimize the server manager dashboard to see the flag folder. Thanks very much